BSides Perth — CTF Writeup
A big thank you to ASD and ACSC for creating this fun CTF. Below is a summary of the challenges I have solved and a short writeup for each. Enjoy 😊
OT
-
1.0 — OT Challenge Start
Soooooo — our powerstation has "sploded. We think it was because we spent last year's maintenance budget on a really bitchin' end-of-year party — but just to be sure we'd like someone to investigate. Fortunately one of our drones from Sector 7-G was running a packet capture on a "Kali" box (whatever that is) when the 'splosion happened. Can you have a squiz at the attached packet capture and just make sure it was our underfunded maintenance budget that was at fault, and not our non-existent security budget that's to blame. kthxbai!!
Question: What is the MD5 of the unzipped file?
Example response:1b000000000000000000000000000000
Answer:1b249a0deb35a7f9f65ddd111594c6de -
1.1 — Understanding the network 1
Question: What is the IP of the powerstation PLC?
Example response:9.87.654.321
Answer:123.123.123.123 -
1.3 — Understanding the comms
Question: What is the IP of the remote, completely non-suss, nothing-to-see-here connection?
Example response:234.456.78.9
Answer:159.100.6.69 -
1.5 — Understanding the System
Question: What is the OT protocol used by the PLC?
Example response:Ping
Answer:Modbus -
1.7 — Recon 3
Question: What is the Function code (int) the attacker used to get this information?
Example response:1
Answer:43 -
1.6 — Recon 2
Question: What is the model name of the targeted PLC?
Example response:DodgyPLC
Answer:SimaticPCS7
How it was solved
modbus as a filter on Wireshark in my Kali was a packet called Read Device Identification which helped me solve the next few challenges.
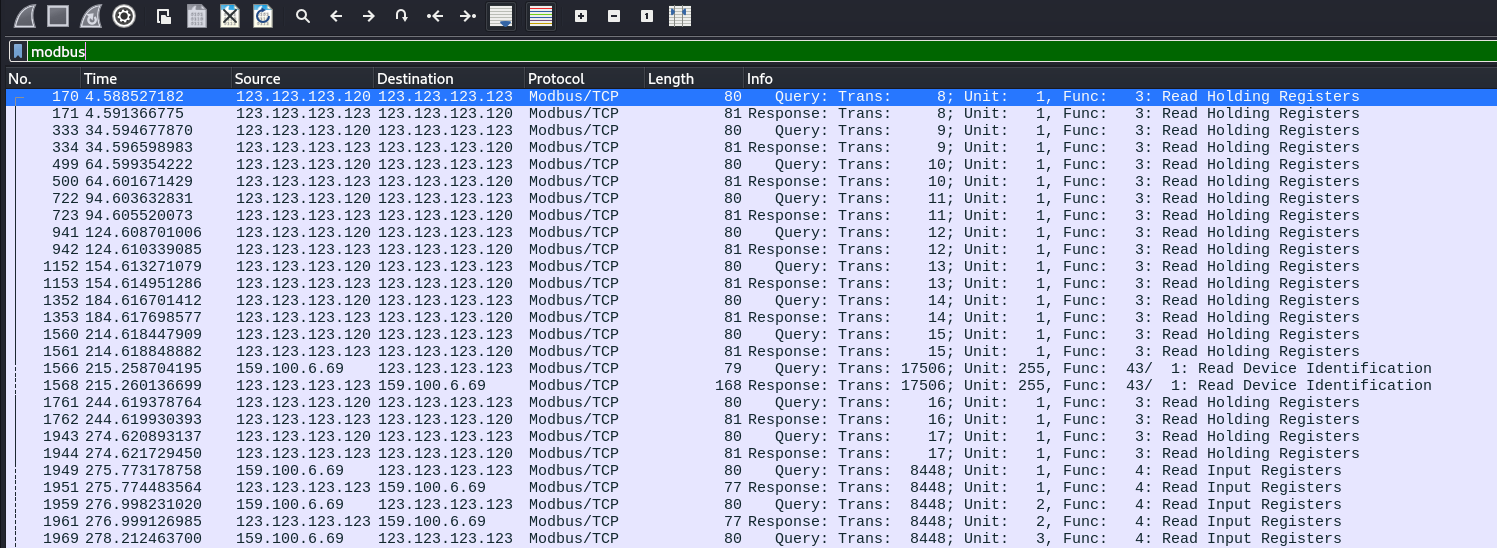
This screenshot was used to solve 1.7 and 1.6
Networking
-
2.0 — Switch Challenge Start
While you're at it — we've received an email telling us that there is some unrelated malicious activity on our switches, and possibly our DC. We've gathered up some artifacts and put them in a zip for you. I'm sure this activity will be fine...
Question: What is the MD5 of the
artifacts.zipfile?
Example response:61D6000000000000000000000000000
Answer:61d659285022dfc19d0553181a0d09b3 -
2.2 — MITRE Framework
Question: What is the MITRE ATT&CK technique number of the technique used to gain initial access to the router?
Example response:T1234
Answer:T1110 -
2.3 — Which Account
Question: Which account was successfully logged into by the actor on the router initially?
Example response:svc_nessus
Answer:operator -
2.9 — Flash
Question: The actor has added malware to the device. What is the filename of this malware?
Example response:evil.exe
Answer:a.tcl -
2.11 — Pivot to Switch
Question: What MITRE technique number was used by the attacker to be able to get onto the switch?
Example response:T1234
Answer:T1078 -
2.5 — Did they also get the admin account?
It looks like they also managed to crack the superadmin account!
Question: What is the password?
Example response:P@ssw0rd
Answer:letmein
How it was solved
I have to be honest this was one of those challenges I solved with the help of a friend, all I really did was spot the hash of the right user which as per the description says
superadminbut as I was on a phone during the first day of BSides (well what could really go wrong) I ended up getting the solved hash from my friend, so a bit of a team effort for that one.